Openssh Vulnerability 2025 Calendar. This flaw permits remote code execution (rce), which can lead to attackers obtaining root access to the system. It affects the default configuration and does not require user interaction, posing a significant exploit risk.
It was discovered that openssh incorrectly handled signal management. Nicknamed as the “regresshion bug”, researchers at qualys initially identified the vulnerability in may 2025.
A signal handler race condition vulnerability was discovered in openssh server (sshd) affecting its default configuration.

OpenSSH Vulnerability CVE20246387 Explained, A signal handler race condition was found in openssh's server (sshd), where a client does not authenticate within logingracetime seconds (120 by default, 600 in old openssh versions), then sshd's sigalrm handler is called asynchronously. This post shares how to find & fix it using the axonius platform.

ciscosaopensshrce2024 Remote Unauthenticated Code Execution, It was discovered that openssh incorrectly handled signal management. Remote unauthenticated code execution vulnerability in openssh server (regresshion):

OpenSSH vulnerability regresshion (CVE20246387) Oderland, The term “regresshion” is a combination of “regression” and “ssh.” A signal handler race condition vulnerability was discovered in openssh server (sshd) affecting its default configuration.

What you need to know OpenSSH RegreSSHion CVE20246387 Hadrian, Openssh versions 8.5p1 prior to 9.8p1 are susceptible to a vulnerability referred to as regresshion which when successfully exploited could lead to disclosure of sensitive information, addition or modification of data, or denial of service (dos). This bug marks the first openssh vulnerability in nearly two decades—an unauthenticated rce that grants full root access.

Strengthening Your Linux Systems Safeguarding Against the Latest, July 2025 cisco security advisory emergency support: Nicknamed as the “regresshion bug”, researchers at qualys initially identified the vulnerability in may 2025.

OpenSSH vulnerability uncovered by researchers, RCE exploit developed, It affects the default configuration and does not require user interaction, posing a significant exploit risk. Cve assigned to this… as of this writing debian and ubuntu have updates out.

New OpenSSH Vulnerability Exposes Linux Systems to Remote Command, A signal handler race condition was found in openssh's server (sshd), where a client does not authenticate within logingracetime seconds (120 by default, 600 in old openssh versions), then sshd's sigalrm handler is called asynchronously. A remote attacker could use this issue to bypass authentication and remotely access systems without proper credentials.

New Vulnerability in OpenSSH Vulnerability CVE20246387 SW Hosting, Cve assigned to this… as of this writing debian and ubuntu have updates out. Learn how to update your systems and enhance security measures to prevent unauthorized access and protect your data.
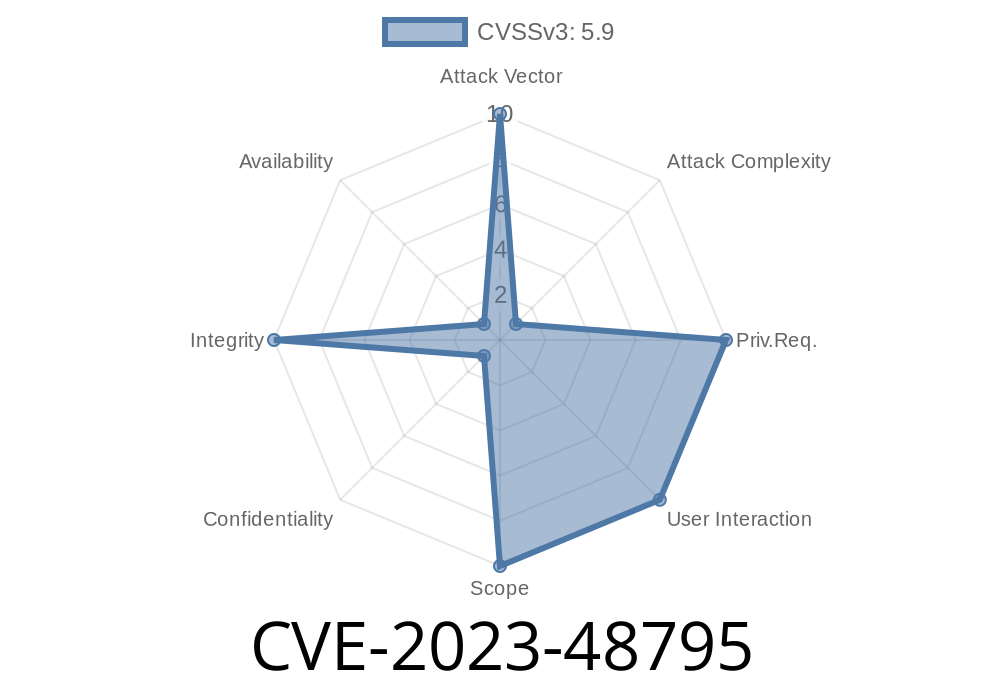
CVE202348795 Terrapin Attack A Dangerous Vulnerability in OpenSSH, Learn how to update your systems and enhance security measures to prevent unauthorized access and protect your data. A remote attacker could use this issue to bypass authentication and remotely access systems without proper credentials.

OpenSSH vulnerability uncovered by researchers, RCE exploit developed, A signal handler race condition was found in openssh's server (sshd), where a client does not authenticate within logingracetime seconds (120 by default, 600 in old openssh versions), then sshd's sigalrm handler is called asynchronously. Learn how to update your systems and enhance security measures to prevent unauthorized access and protect your data.
A severe vulnerability in openssh’s server (sshd) has been uncovered by qualys’ threat research unit (tru), potentially affecting over 14 million linux systems worldwide.